- Home
- About Us
- Recovery Services Individual RecoveryEnterprise RecoveryAdditional Recovery
- Software
- Testimonials
- Locations
Forensic data recovery in employment claim
When our client's server was physically damaged by an employee they approached us to forensically investigate!
Identifying electronic evidence from a damaged RAID server...
After our client’s mail server stored on a RAID-5 was maliciously damaged by one of their employees, we were instructed by their solicitor to conduct a full forensic examination of the evidence. It was suspected that the server’s hard drives were concealing inappropriate correspondence. The hard drives had been removed and the circuit boards, physically destroyed. To exasperate the situation, backups had been securely erased and could not be retrieved.
Our technicians removed the RAID server from site to ensure preservation of the evidence. Before acquisition and analysis could begin, it was necessary to render the hard drives serviceable in order to take an exact sector level duplicate. We are one of the few computer forensic experts that also specialise in data recovery. The hard drives were dismantled in our clean room and rebuilt using donor parts.
SSD vs. HDD – Data Destruction and Asset Disposal
Why care about data destruction and asset disposal? According to the US Department of Commerce, data security breaches cost US companies more than $250 billion per year! A few examples will help illustrate the importance of proper data erasure and asset disposal practices.
A Loyola University (Chicago) computer with the Social Security numbers of 5,800 students was discarded before its hard drive was erased, forcing the school to warn students about potential identity theft.
A survey by data forensics experts, Garfinkel and Shelat, found that over 40 precent of hard drives collected from eBay and other places had recoverable data and over 30 percent contained sensitive information, including credit card numbers.
A BBC documentary revealed that bank account details of potentially thousands of UK residents were being sold in West Africa for less than £20. Sensitive information was contained on the PC hard drives exported to Nigeria (2006).
Data is stored magnetically on traditional hard disks (HDDs). As the read/writes heads pass over the magnetic substrate, bits of data are magnetically aligned and oriented in such a way that they can be interpreted as 0’s and 1’s (binary data). A collection of these bits of data are put together to form bytes which are in turn grouped together in what is traditionally referred to as a sector (usually 512 bytes of data).
Change boot settings from a VM BIOS
Often overlooked, a VM's BIOS is more limited than a physical machine's BIOS, but will allow you to adjust boot settings.
Virtual machines are logical representations that are designed to mimic physical hardware. Consequently, VMs have many of the same attributes as a physical machine, including things like network ports, memory, and virtualized CPU instances. One aspect of a virtual server that is often completely overlooked however is its BIOS.
In a way, this is completely understandable. After all, it's usually possible to get a virtualized workload up and running without ever touching the VM BIOS. Besides, it's easy to assume that virtual servers either don't have a BIOS or that they simply use a pass through BIOS that leverages the physical server's BIOS. However, there are actually some BIOS settings that can be configured for VMs.
These settings depend on two main factors. The first of these factors is the hypervisor. Each hypervisor vendor chooses for itself the settings they want to expose.
The second factor is the VM generation. Different generations of VMs interact with the hardware in different ways, and the hypervisor therefore exposes different settings based on the VM generation.
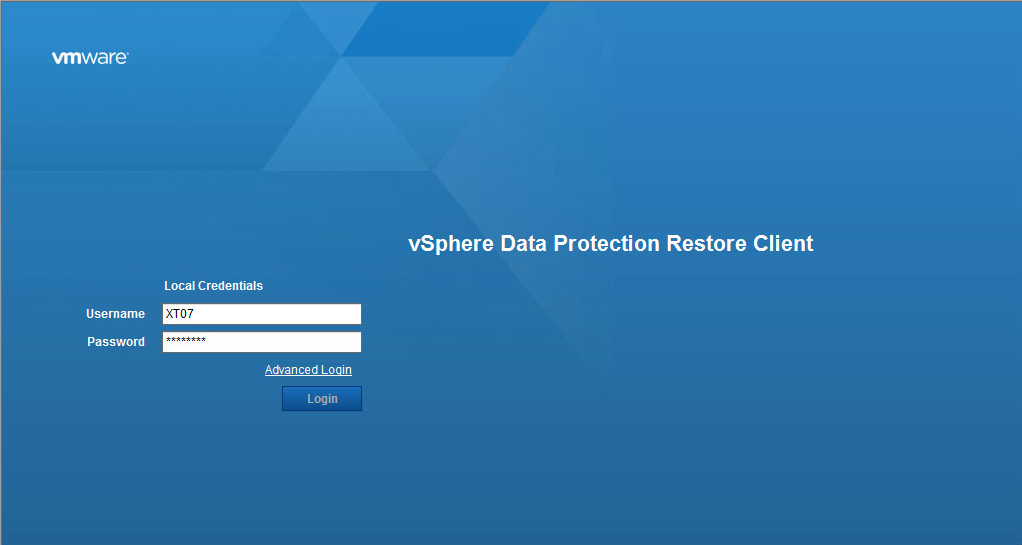
How to use VMware VDP Restore Client for file recovery
You may have noticed during the VMware VDP appliance setup you visited every VDP configuration tab, but did not encounter an option to restore files or folders that been backed up. This is because you cannot do this from the vCenter web client. In order to do this task you need to use what VMware calls the “vSphere Data Protection Restore Client.”
The VDP Restore Client is also a web client, but it must be accessed from one of the VMs that are being backed up and the VM needs to have VMware tools installed in order to be able to perform any successful restore.
Remember, in order to configure the VDP appliance for first use you need to visit this URL.
Copyright © 2025 DataRecoup Recovery Services. All Rights Reserved. Designed by DataRecoup Lab.




