- Home
- About Us
- Recovery Services Individual RecoveryEnterprise RecoveryAdditional Recovery
- Software
- Testimonials
- Locations

Tips and Hints (29)
 Dictionary of terms
Dictionary of terms
Because some components of hard disk drive that play a key role in its operation are usually perceived as an abstract concepts, below you will find a list and description of the most important terms that will make things clear about hard disk drive.
Aссes time — a period of time required by the drive on hard disk to seek and transfer data from or into the memory. Speed of drives based on hard magnetic disks is usually determined with access time (fetch time).
Сluster — smallest unit of space with which file allocation table works. As rule, cluster consists of 2-4-8 or more sectors.
 Frankly speaking, in many situations the recovery of fragmented files is not something difficult to do, subject to availability of a relevant record about the file in the file system. In reality, the direct task of the file system is to store information about where and in which order sectors containing file’s contents are located on the disk. That is why recovering recently deleted file won’t be a problem.
Frankly speaking, in many situations the recovery of fragmented files is not something difficult to do, subject to availability of a relevant record about the file in the file system. In reality, the direct task of the file system is to store information about where and in which order sectors containing file’s contents are located on the disk. That is why recovering recently deleted file won’t be a problem.
However, the situation is different when the file system is damaged or destroyed, like, for example, in case of formatted disk. In such circumstances modern data recovery tools use signature-based search algorithms that read all data from the disk surface in order to detect known types of files.
 Protection against data leaks Ξ Data leaks and self-protection
Protection against data leaks Ξ Data leaks and self-protection
Over one hundred million people are exposed to the risk of personal data theft. It means that all those people can become target of phishing.
Well known personal data leaks, for example, data leaks of users of Sony consoles in 2011 or Target network got into the headlines of mass-media only because of its scale. Experts believe that data leaks occur constantly and millions of unaware people are exposed to them.
I.e. there are no safe networks and people have to fight it themselves.
If one approaches the problem with a clear head you will see that none of the companies or organizations working in the network can guarantee protection of your information. And, perhaps, would never be able to, no matter how often it would talk about it.
 Virtualization offers huge opportunities for companies of any scale. On the other hand, virtual infrastructure poses before a company a number of serious difficulties, including increased risk of massive failure and data loss.
Virtualization offers huge opportunities for companies of any scale. On the other hand, virtual infrastructure poses before a company a number of serious difficulties, including increased risk of massive failure and data loss.
But these problems can be taken care of by finding the right solution. Ideally, it should solve the following seven tasks:
- Flexibility choosing provider. When purchasing the solution for backup copying and recovery, a company should not stop on one provider. Better prefer an economical software package for backup, emergency recovery and data migration between different hypervisors, allowing to work with incompatible systems and different web-sites, as well as using products from several providers. The best is to choose a flexible solution, because offers of one or several brands may be effective.
Introduction
There are many problems in the sphere of ensuring business continuity related to fast increase of data in modern IT infrastructures. Here we outline two main:
- How to plan a place to store large data volumes?
- How to backup these data?
And yes, increase in data volume in terabytes a year at some large company is quite a real scenario today. But, what about effective storage and backups? There are maximum 24 hours in a day and the gap of backing up cannot go up forever (in contrast to data). Today we would like to tell you how deduplication may help you to ease this problem.
Deduplication
In a broad sense, there are two main types of deduplication:
- File-level deduplication – deduplication unit in this method is a separate file, when duplicating files are excluded from data storage system. When they say about file-level deduplication, often they also mention Single-Instance Storage (SIS) technology.
- Block-level deduplication – here deduplication unit is a data block of random length, that is often repeated in different logical objects of data storage system.
Usually, the more granular deduplication scheme is used, the more space in data storage is being saved.
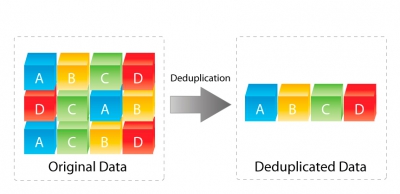
What is Single-Instance Storage (SIS)? The principle of method is simple, for example, if there are two files that are identical, then one file is replaced with a link to another one. Such mechanism successfully works in mail servers (for instance, Exchange) and in databases. For example, if one user of corporate mail forwards a letter with an attached file to several recipients, then this file will be saved in Exchange base only once.
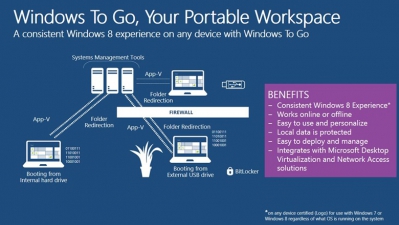 Windows To Go (WTG) is one of the new features of Windows 8 that allows creating a duly configured image of OS with installed necessary software that will boot directly from USB drive regardless of what OS is installed on computer to which this USB drive is going to be connected.
Windows To Go (WTG) is one of the new features of Windows 8 that allows creating a duly configured image of OS with installed necessary software that will boot directly from USB drive regardless of what OS is installed on computer to which this USB drive is going to be connected.
Why is that necessary?
Direct result of application of WTG is a bootable USB drive (flash drive or external HDD) which contains fully operations and ready-to-use Windows 8. Fully operational means that this OS is duly configured in accordance with the requirements of organization: included in domain, if necessary, group policies are applid to it, including security policies, patches, remote access technologies are set (VPN/DirectAccess), required set of software is installed, etc. Simply connect the drive to a computer compatible with Windows 7 or Windows 8 and boot right from it. At the same time you will get your personal OS with all settings and there is no way you impact an OS installed on a hard disk drive of such computer.
Accordingly, WTG refers to corporate features of Windows 8, i.e. targeted towards use in the company. Most apparent WTG use scenarios are the following:
- Mobile employees. Employees that, for example, often move between company’s offices and are in need of access to corporate network using their own settings, documents, etc. So, having along a tiny external hard disk drive or even a pen drive instead of two-three kg laptop may seem quite an attractive option for many. While visiting another office it is enough to insert your drive into an appropriate computer.
- Temporary employees, working, for example, on any project. Such employee might have his/her own laptop that in no way meets the safety requirements of your network. Equip an employee with prepared drive with WTG image and this employee will be able to use your image on his/her laptop to work on the project.
- Employees with non-permanent workplace (or working in shifts), that nevertheless need to access corporate network in office of outside the office.
- Work from home. If necessary, employee can boot home PC with WTG image and get access to corporate network and to business apps.
 If you aren’t already using an antivirus/firewall (av/fw) program, or the free trial that came with your computer is running out, you’re likely considering going with one of the industry’s heavy hitters: Symantec, Kaspersky, McAfee, or Trend Micro. These are not necessarily the best choice for you, though. Just because a solution is free or is not widely known, doesn’t mean that it’s not a good program.
If you aren’t already using an antivirus/firewall (av/fw) program, or the free trial that came with your computer is running out, you’re likely considering going with one of the industry’s heavy hitters: Symantec, Kaspersky, McAfee, or Trend Micro. These are not necessarily the best choice for you, though. Just because a solution is free or is not widely known, doesn’t mean that it’s not a good program.
One thing you do need to understand of pretty well every av/fw solution that is on the market - whether it is a paid version or a free version - you will be inundated with ads. Every company wants to make money. If you get a free version, you will be given offers for the paid version. If you get the paid version, you will be given offers for the ultimate paid version. If you get the ultimate paid version, you will be given offers for expert computer assistance subscriptions. As horrible as it sounds, internet security software makers prey upon the users who are not computer savvy, using their lack of knowledge and fear of the unknown to make users believe that they NEED the more expensive program and the one-on-one assistance offered as an additional fee.
There are two very important things to remember when considering the right internet security protection for your computer. Number one, it is important to chose a robust program that includes the features that you need. Number two, it is important that fear does not get the best of you. Make informed decisions, and do not ever trust the word of a random person on the other end of the line that is trying to get you to buy a service - at least in regards to your computer’s security and health. If you believe your computer has a virus, take your computer to a local repair shop (I do not recommending using big chains - go local!) and see what they have to say.
 Computer users in any country of the world perform similar tasks and majority of computers have similar software installed: various editors (text, table, graphic, audio and video), browsers, players, archivers, antiviruses, image viewers, etc.
Computer users in any country of the world perform similar tasks and majority of computers have similar software installed: various editors (text, table, graphic, audio and video), browsers, players, archivers, antiviruses, image viewers, etc.
Under such ‘total’ use of similar software, its file formats inevitably become popular and most used. Below you will find a short list of most common file formats.
Table of file formats and software for creation/editing of these types of files
 When you think of VPN, the first thing that usually comes to mind is work. Many big corporations use VPNs to provide access to confidential work documents, and to allow their employees to safely work remotely. What many people don’t realize is that VPNs are your #1 defense on the internet.
When you think of VPN, the first thing that usually comes to mind is work. Many big corporations use VPNs to provide access to confidential work documents, and to allow their employees to safely work remotely. What many people don’t realize is that VPNs are your #1 defense on the internet.
VPN stands for Virtual Private Network. Much like physical private networks (ie your work’s intranet), VPNs keep the data you’re sending and receiving private. The majority of VPNs also encrypt your data, meaning that even if it were to be intercepted, it would not be useful.
Security Risks Online
The security risks that are present on the internet are nearly uncountable. From phishing scams that try to get your usernames and passwords or personal and financial information to sales scams to loan scams. If someone out there thinks they can benefit from making a victim out of you, they will try it at least once. We’d all like to think that we are smart enough to fall for a scam. Many people believe that they do not have enough money that anyone would want to target them for a scam. Unfortunately, neither of these are true.
 We’ve all heard of it. In fact, we all use it, even if you don’t know you’re using it. The Cloud makes life easier. One of the problems with defining the cloud is that it is a new and growing idea. As new providers and new technologies emerge, the definition of the cloud computing changes.
We’ve all heard of it. In fact, we all use it, even if you don’t know you’re using it. The Cloud makes life easier. One of the problems with defining the cloud is that it is a new and growing idea. As new providers and new technologies emerge, the definition of the cloud computing changes.
Essentially, “the Cloud” is a storage space or service available from anywhere you have an internet connection. One of the first things that likely comes to mind is email. Web-based email, like Gmail, Yahoo Mail, or Hotmail, store your emails “online”. Your emails do not need to be downloaded to your computer to be read, the way that email was way-back-when in the days of ISP mail and Outlook. Of course, you can opt to download your emails, if you know how, so you can keep a local copy, but most users don’t ever do that. Even though you say your email is ‘online’, it is actually on a server somewhere that is always connected to the internet, and is accessible to you, from any device that has an internet connection and a browser (or an app!). In other words, your email is in The Cloud.
Much of what we do online today is in “the Cloud.” Though it’s not likely to come to mind, social networking sites are in the cloud: Facebook, Instagram, Twitter, YouTube, etc. All of the data that you use, save, and access is not saved locally on your computer, but instead on a server somewhere specifically designed for that social media platform. There are also a variety of hosting services available that you likely utilize that keep your data in ‘the cloud’: Google drive (or Google docs, if you’re like me and still call it that), Office 365, Photobucket, Flickr, etc. These services allow you to upload and save files so you can access them from any location that has internet. Certain services, like Google Drive for example, allow you to upload nearly any type of file you could want to store as well as offering ‘office’ services (documents, spreadsheets, forms, presentations) that can be created directly from the service itself.
Copyright © 2024 DataRecoup Recovery Services. All Rights Reserved. Designed by DataRecoup Lab.


 Protection against data leaks Ξ Data leaks and self-protection
Protection against data leaks Ξ Data leaks and self-protection